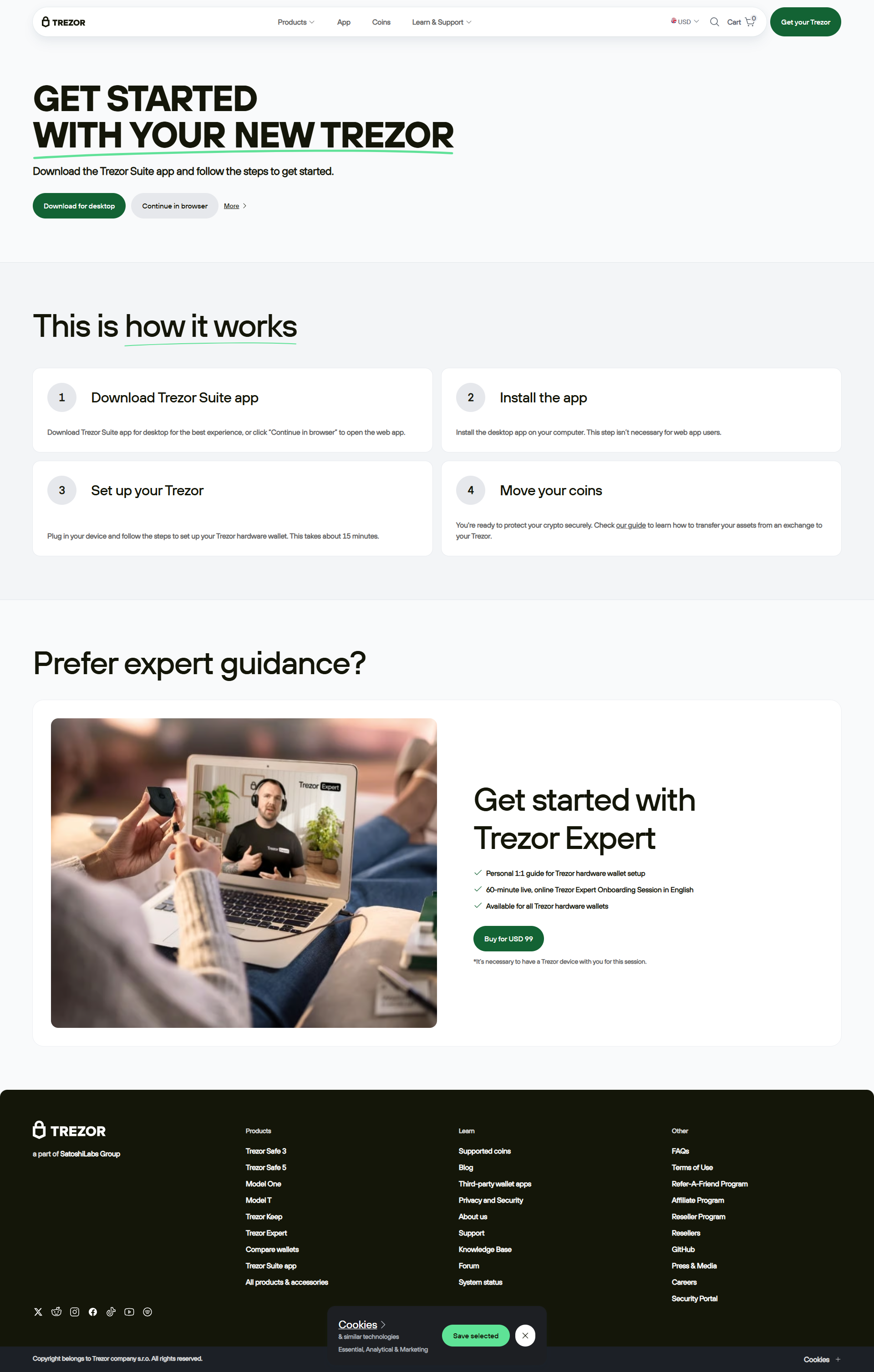
Trezor Login – Securely Access and Manage Your Crypto Portfolio
A complete, step-by-step guide to using Trezor Login to keep your digital assets safe, private, and always within your control.
🔐 What Is Trezor Login?
Trezor Login is the secure authentication process that allows users to access their hardware wallets and manage cryptocurrencies via Trezor Suite or the Trezor.io/Start portal. By requiring physical confirmation from your device, it ensures that only you can authorize access to your funds — even if your computer is compromised.
⚙️ How Trezor Login Works
Step 1: Connect Your Device
Plug in your Trezor hardware wallet (Model One or Model T) using the USB cable. The device will power on automatically.
Step 2: Open Trezor Suite
Launch Trezor Suite on your desktop or access it through Trezor.io/Start to begin the authentication process.
Step 3: Verify on the Device
Check your Trezor’s screen for login requests and confirm only those you initiate. Never trust browser pop-ups or third-party prompts.
Step 4: Enter Your PIN
Use the randomized PIN matrix displayed on your Trezor device to enter your PIN securely — ensuring no one can keylog or intercept it.
🧩 Why Trezor Login Is the Ultimate Security Layer
Trezor Login protects your crypto assets using hardware-level encryption and physical confirmation. Unlike browser extensions or web wallets, it isolates your private keys from online systems. Every transaction must be verified on your device screen, preventing unauthorized access. It’s like using a physical key for your bank vault — no digital thief can copy it.
🚀 First-Time Trezor Login Setup
- Unbox your Trezor and connect it to your computer.
- Visit Trezor.io/Start and download the Trezor Suite app.
- Install any pending firmware updates on the device.
- Create a new wallet and safely store your 24-word recovery seed.
- Set up a strong PIN and optional passphrase for added protection.
- Login to confirm your setup — your wallet is now ready to use.
📊 Trezor Login vs. Ledger Login: A Quick Comparison
| Feature | Trezor Login | Ledger Login |
|---|---|---|
| Source Code | Fully open-source and auditable | Closed-source firmware |
| Interface | Trezor Suite – intuitive and minimalist | Ledger Live – detailed analytics |
| Security Type | PIN + on-device verification | PIN + secure element chip |
| Ideal User | Privacy-focused individuals | Advanced and institutional traders |
💡 Best Practices for Using Trezor Login Safely
- Always verify the official Trezor.io domain before connecting.
- Keep your recovery seed phrase offline and secure.
- Enable the passphrase feature for additional wallet layers.
- Update firmware regularly through Trezor Suite.
- Avoid public or shared computers for crypto operations.
🧠 Troubleshooting Common Trezor Login Issues
1️⃣ Device Not Detected
Try reconnecting your device or using a different USB cable. Ensure that Trezor Bridge is installed on your system.
2️⃣ PIN or Passphrase Error
Check the randomized layout on your Trezor’s display — each login session shuffles the keypad for better security.
3️⃣ Firmware or Suite Outdated
Visit the settings section in Trezor Suite to download the latest firmware updates and improve performance and compatibility.
💬 Frequently Asked Questions
Q1: Can I use Trezor Login without the device?
No. Physical confirmation is mandatory to prevent remote hacking.
Q2: Is Trezor Login compatible with mobile devices?
It primarily supports desktops but can work with mobile OTG adapters on Android.
Q3: What happens if I lose my Trezor?
You can recover your assets using your seed phrase on a new device. Keep your seed private and offline.
🚀 Final Thoughts on Trezor Login
Trezor Login isn’t just an access point — it’s a fortress for your cryptocurrency. With its physical authentication, open-source transparency, and secure design, it’s an essential tool for anyone serious about digital finance. Protect your keys, own your future, and log in with confidence.